
(http://www.grc.com/stevegibson.htm).
The site contains many ultra-small assembly tools to patch/fix XP holes and beef up network security, as well as handy gizmos for turning off monitor from a shortcut on the desktop etc.
http://www.grc.com/default.htm
Mostly:
DCOMbobulator - 29KBytes

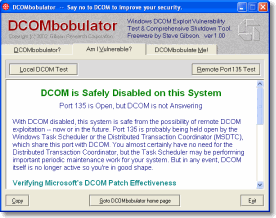
Effortlessly Tame Windows Dangerous DCOM Facility
Microsoft's DCOM security patch leaves DCOM running, open, and waiting for the next malicious exploit. DCOMbobulator allows any Windows user to quickly check their system's DCOM vulnerability, then simply shut down the unnecessary DCOM security risk."
http://www.grc.com/files/DCOMbob.exe
Shoot The Messenger - 22KBytes


"Windows Messenger Spam Elimination Freeware
In addition to being a security risk, Windows' "Messenger Service" is being used to "Spam" Windows users across the Internet.This utility gives users immediate control over the Windows Messenger service."
http://www.grc.com/files/shootthemessenger.exe
UnPlug 'n Pray - 22KBytes



"Instantly and Easily Control Windows' Insecure, Exploit-Prone and Probably Unnecessary Universal Plug and Play Network Support"
http://www.grc.com/files/unpnp.exe
IDServe 1.0 - 26KBytes

Internet server identification utility
http://www.grc.com/files/idserve.exe
"HTTP Server Identification: As stated above, and as shown in the sample screen shot above, ID Serve can almost always identify the make, model, and version of any web site's server software. This information is usually sent in the preamble of replies to web queries, but it is not shown to the user.
Non-HTTP Server Identification: Most non-HTTP (non-web) Internet servers (like FTP, SMTP, POP, NEWS, etc.) are required to transmit a line containing a numeric status code and a human readable greeting to any connecting client. So ID Serve can also connect with non-web servers to receive and report that server's greeting message. This generally reveals the server's make, model, version, and other potentially useful information.
Reverse DNS Lookup: As shown in the image above, most ID Serve users will enter a site's or server's domain name or URL. ID Serve will then use the domain name system (DNS) to determine the IP address for that domain. But sometimes it's useful to go in the other direction to determine the domain name associated with a known and provided IP. This process, known as "reverse DNS lookup", is also built into ID Serve. Simply enter any IP address and ID Serve will attempt to determine the associated domain name.
Simple Cookie Scout: If you are curious about the appearance, format, expiration, and use of a web site's browser cookies, ID Serve can be a convenient way to examine a web site's cookies without either providing or accepting that site's cookies. Simply scroll back through the "Server query processing" window to examine the "Cookie:" header lines sent by the site's web server.
Simple Port Probe: ID Serve uses the standard Windows TCP protocol when attempting to connect to a remote server and port. Just like our ShieldsUP! port probe, ID Serve will display either connection success (an open port), or connection failure. In the event of a connection failure, ID Serve determines and displays whether the port is closed or stealth. ID Serve can, therefore, be used as a simple probe of any port on any remote machine."
http://www.grc.com/files/idserve.exe
Firewall Leakage Tester 1.2 - 25KBytes

"WinXP's built-in firewall does not attempt to manage or restrict outbound connections at all. It appears to be a useful firewall for hiding the machine from the Internet (it has "stealth mode" unsolicited packet handling), but you will still need to use a good third-party personal firewall if you wish to manage and control outbound connections from your system."
http://www.grc.com/files/leaktest.exe
Shields UP! - Excellent web-based port/security test
https://www.grc.com/x/ne.dll?bh0bkyd2
WIZMO - 35KBytes
http://www.grc.com/files/wizmo.exe
Command-Line Assembly Tool
[Wizmo Command Vocabulary]
SHUTDOWN TRIGGER COMMANDS
standby — trigger Windows' standby mode
Example: wizmo standby
hibernate — triggers Window's long-term hibernation
Example: wizmo hibernate
logoff — log off the current user
Example: wizmo logoff
reboot — restart (reboot) the computer
Example: wizmo reboot
shutdown — shutdown the computer
Shuts down all of the user's running programs, exits Windows, then powers off the machine if supported by the system's hardware.
Example: wizmo shutdown
DRIVE COMMANDS
open — opens the system's default CDROM drive tray.
Example: wizmo open
close — closes the system's default CDROM drive tray.
Example: wizmo close
open={drive:} — open or eject specific removable drive media.
Example: wizmo open=w:
close={drive:} — close or load specific removable drive media.
Example: wizmo close=r:
WINDOWS SCREEN SAVER COMMANDS
blank — activate the system's screen saver
Example: wizmo blank
autoblank={0|1} — disables/enables timed blanking
Example: wizmo autoblank=0 (disable timed blanking)
WIZMO'S SCREEN SAVER COMMANDS
blackout — blank the screen to "basic black"
Example: wizmo blackout
desktop — blank the screen to "desktop" color
Example: wizmo desktop
monoff — turns off all monitors
Example: wizmo monoff
graviton — activate Wizmo's animated screen saver
Example: wizmo graviton
shake={0-??} — set Wizmo unblanking mouse sensitivity
Example: wizmo shake=0 graviton
AUDIO CONTROL COMMANDS
quiet — suppress the "Gibson sigh" Wizmo sound
Example: wizmo quiet desktop
volume={0-100} — set the system's audio level
Example: wizmo volume=90 monoff volume=20
play={wavefile} — play the specified file
Example: wizmo play=c:\windows\media\chimes.wav
wave={0-100} — set the system's wave file audio level
Example: wizmo wave=25
mute={0|1} — control the system's audio muting
Example: wizmo mute=1
No comments:
Post a Comment